Maze ransomware group has published personal and medical details of thousands of former patients of a medical research firm. This follows a ransomware attack on the business.
The Maze ransomware group attacked the computer systems of Hammersmith Medicines Research (HMR) in March. They published personal details of thousands of former patients after the company declined to pay a ransom.
The company carries out trials to develop the Ebola vaccine and drugs to treat Alzheimer’s disease. The firm performs early clinical trials of drugs and vaccines.
The cyber-crime group published HMR’s medical files only days after the Maze crime group made a public promise not to attack medical research organisations during the coronavirus pandemic. HMR said that IT staff discovered a “severe attack” in progress but were able to stop it and restore their computer systems and email services by the end of the day.
The hacking group published a notice on a website claiming it had attacked the company with ransomware on 14th March. It increased the pressure on the organisation on the 21st March. Maze published historic sensitive, medical and personal information about thousands of former patients on the internet.
The files according to HMR said are likely to date back between 8 to 20 years The files contain medical questionnaires, copies of passports, driving licenses and national insurance numbers. It is thought that more than 2,300 of the organisation’s patients records could be affected.
It has been established that the documents, were a sample of HMR former patients. Those chosen have surnames beginning G, I and J, include at least one copy of a currently valid passport.
Ransom demand received
Boyce said that the hackers had sent the company medical files of former patients which were 8 to 20 years, The files were sent as proof they had gained access to the company’s data, along with a ransom demand.
He said that most of the sample files sent to HMR contained details of young people who had taken part in clinical trials. These people had done so whilst travelling and would be difficult to trace.
“What they have sent us was 8 to 20 years old, and we would not know how to contact them. They are probably young people who have mostly returned to their country of origin,” he said. “They are from Australia and South Africa, which were frequent visitors to this country and at this time took part in clinical trials.” Computer Weekly quoted Boyce as saying.
Boyce said he was aware that the hackers had released further records on the internet, but had not seen their content. The research company is not a pharmaceutical company and does not have the funds to pay a ransom demand even it wanted to, Boyce added.
“We have no intention of paying. I would rather go out of business than pay a ransom to these people,” he said.
Maze breaks promise not to attack medical organisations
The Maze Group first came to notice in May 2019, extorts victims by encrypting the files of an organisation and demanding a ransom payment to release the files. It increased the pressure in late 2019 by naming companies on websites that refused to pay ransoms. It also published documents and data stolen from their computer networks.
The group made a public promise in a ‘press release’ reported by Tech Target on 18th March. They stated that they would not attack medical organisations during the coronavirus outbreak.
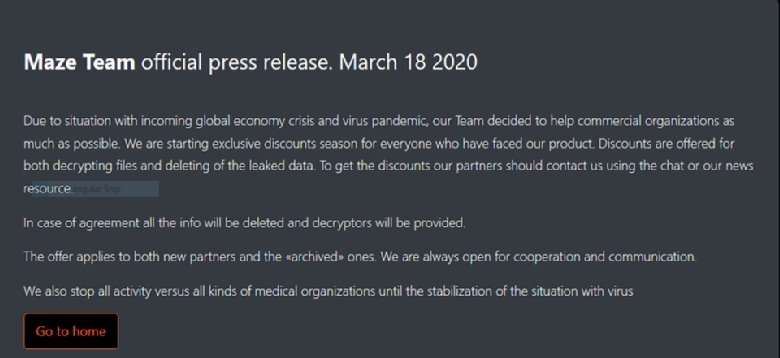
“Due to [the] situation with the pandemic, our team decided to help commercial organisations as much as possible. We are starting exclusive discounts season for everyone who has faced our product,” it said.
“We also stop all activity versus all kinds of medical organisations until the stabilisation of the situation with the virus.”
Criminals ‘only interested in money’
Maze’s apparent reversal of its policy not to attack medical intuitions shows that the criminals’ only focus was to make money. Raj Samani, chief scientist at computer security specialist McAfee had said.
“We have had previous assertions from other ransomware groups that they aren’t going to go after medical environments. However, it really shows us we can’t take what these individuals say as trustworthy,” he said.
HMR’s Boyce said: “They are unscrupulous individuals and they are pretending now that there is an amnesty because of the Covid-19 virus.”
ICO to investigate
HMR has reported the incident to the Information Commissioner’s Office (ICO). They told Computer Weekly that it is making enquires.
An ICO spokesperson said: “People’s medical data is highly sensitive information. People expect it to be handled carefully and securely. Organisations also have a responsibility under the law.
“When a data breach occurs, we would expect an organisation to consider whether it is appropriate to contact the people affected. They should also consider whether there are steps that can be taken to protect them from any potential adverse effects.”

0 Comments